Microsoft Azure
![]()
Transition to the Cloud with Our Expert Microsoft Azure Migration Services
Unlock the full potential of your IT infrastructure with Microsoft Azure. Transition effortlessly to the cloud, enhancing operational agility and fortifying your security posture. Azure provides robust backup solutions and automated disaster recovery, eliminating the need for additional hardware and reducing downtime risks. Gain comprehensive control over identity management, whether on-premises or in the cloud. Elevate your business operations and drive innovation by leveraging Azure’s advanced capabilities. As a trusted Microsoft Partner, we specialize in planning, implementing, and managing Microsoft Azure cloud migrations. Our expertise ensures a smooth transition to the cloud with minimal disruption and maximum benefit, guiding you every step of the way from planning to execution and ongoing support.

Why Choose Microsoft Azure
Microsoft Azure stands out as a premier cloud platform, offering a comprehensive suite of services to transform your IT infrastructure. With Azure, you gain access to industry-leading tools for computing, analytics, storage, and networking. Azure’s hybrid capabilities and seamless integration with existing on-premises systems provide unmatched flexibility. The platform’s advanced security features, including multi-layered protection and compliance with international standards, ensure your data and applications remain secure. Azure’s scalable infrastructure allows you to adapt to changing business demands, optimizing performance and efficiency. Embrace Azure to drive innovation and achieve operational excellence.

Key Benefits of Migrating to Azure
Migrating to Microsoft Azure offers numerous advantages tailored to meet business needs:
- Comprehensive Security: Leverage Azure’s advanced security framework, featuring multi-factor authentication, threat intelligence, and extensive compliance certifications to safeguard your digital assets.
- Operational Efficiency: Enhance productivity by streamlining processes and reducing IT overhead with Azure’s integrated management tools and automated solutions.
- Business Continuity: Ensure seamless operations with Azure’s robust disaster recovery and backup solutions, minimizing downtime and maintaining business continuity even in adverse situations.
- Scalability: Effortlessly scale your IT resources up or down based on your organization’s needs, ensuring optimal performance and cost management.
- Cost Management: Benefit from Azure’s pay-as-you-go pricing model, providing flexibility and financial efficiency by only paying for the resources you use.

Infranet’s Azure Migration Services
Infranet offers a holistic approach to Azure cloud migration, tailored to meet the unique requirements of small to mid-sized enterprises. Our service offerings include:
Detailed Assessment and Strategic Planning: We begin with a thorough evaluation of your current IT infrastructure, identifying key areas for improvement and developing a strategic migration plan that aligns with your business goals. Our interactive readiness assessment helps pinpoint specific needs and readiness for cloud migration.
Seamless Migration Execution: Our experienced team ensures a smooth transition of your data, applications, and workloads to Azure. We minimize downtime and disruptions, leveraging best practices and advanced tools to migrate efficiently.
Comprehensive Post-Migration Support: Post-migration, we provide ongoing support and optimization services. Our team continually monitors your Azure environment, ensuring peak performance and addressing any issues promptly to maintain operational excellence.
Choose Infranet as your partner for Azure migration to leverage our expertise and ensure a secure, efficient, and seamless transition to the cloud.
Networking

A Next-Generation Architecture That Accelerates Business Innovation
We work, live, play, and learn in a world that has no boundaries and knows no borders. Cisco Borderless Networks securely, reliably, and transparently connects people, information, and devices. As applications and services are increasingly offered and consumed from beyond the traditional enterprise perimeter, Cisco Borderless Networks transparently integrates cloud services and embedded network services with integratedpolicy and management to deliver the borderless experience.
Switching
Get more than connectivity with Cisco Borderless Networks in your LAN. Expect more from your network and save more on operations through innovations such as Cisco EnergyWise.
Routing
Enhance productivity and minimize total cost of ownership with next-generation routing solutions that deliver a superior customer experience, increased architectural scalability, and investment protection.

There is a high rate of change in the mobility industry, making it difficult for yesterday’s networks to adapt. With the growth of bandwidth-intensive applications such as high-definition video and bring-your-own-device (BYOD) trends, for example, the IT manager’s job has suddenly grown more complicated and requires advanced wireless solutions.
In order to address these emerging trends, Cisco has evolved its line of Wi-Fi access points with a new-generation of access points. These access points extend spectrum intelligence, antenna density, and client acceleration to new price points in the mainstream. The product line also offers options that support the latest IEEE Wi-Fi standard, 802.11ac. The second generation Cisco Aironet Access Point portfolio addresses a broad range of requirements for enterprise-class wireless services and provides industry-leading performance for secure and reliable radio-frequency (RF) connections. Whether you require entry-level wireless connectivity for a small enterprise, mission-critical coverage at thousands of locations, or best-in-class performance with investment protection for high-density environments, you can rely on Cisco’s broad access point portfolio.

Cisco Meraki cloud-managed edge and branch networking solutions simplify enterprise-class networks. Wireless, switching, security, and devices are centrally managed from the cloud, In this way, Meraki gives network administrators visibility and control, without the cost and complexity of traditional architectures.
Wireless
Ultra-high performance, up to 900 Mbps
Integrated wireless security and guest access
Cloud-based management eliminating the need for controller hardware
Security Appliances
Provides complete networking, security, and application control
Centrally managed through the cloud
Includes WAN optimization, VPN, firewall, and branch routing
Access Switches
Offers 24 and 48 port Gigabit Ethernet models with PoE on all ports
Centrally managed with monitoring and alerts
Optimized for voice and video traffic
Hosted Collaboration

Collaboration

IP telephony provides a way for you to extend highly secure, reliable, and consistent communications services to all your employees whether they are in main campus locations, at branch offices, working remotely, or are mobile. IP telephony transmits voice communications over the network using open-standards-based Internet Protocol.
Cisco IP telephony solutions are an integral part of Cisco Unified Communications, which unify voice, video, data, and mobile applications on fixed and mobile networks enabling users to easily communicate in any workspace using any media, device, or operating system. Using the network as the platform, Cisco IP telephony solutions help organizations of all sizes realize greater security, resilience, and scalability in addition to the inherent benefits of using a converged network for transport and interconnection.

Unified messaging (or UM) is the integration of different electronic messaging and communications media (e-mail, SMS, fax, voicemail, video messaging, etc.) technologies into a single interface, accessible from a variety of different devices. While traditional communications systems delivered messages into several different types of stores such as voicemail systems, e-mail servers, and stand-alone fax machines, with Unified Messaging all types of messages are stored in one system. Voicemail messages, for example, can be delivered directly into the user’s inbox and played either through a headset or the computer’s speaker. This simplifies the user’s experience (only one place to check for messages) and can offer new options for workflow such as appending notes or documents to forwarded voicemails.
Cisco Unity Connection Data Sheet
SpeechView Text-to-Speech Data Sheet
Cisco IM and Presence consists of many components that enhance the value of a Cisco Unified Communications system. The main presence component of the solution is the Cisco IM and Presence Service, which incorporates the Jabber Extensible Communications Platform and supports SIP/SIMPLE and Extensible Messaging and Presence Protocol (XMPP) for collecting information regarding a user’s availability status and communications capabilities. The user’s availability status indicates whether or not the user is actively using a particular communications device such as a phone. The user’s communications capabilities indicate the types of communications that user is capable of using, such as video conferencing, web collaboration, instant messaging, or basic audio.
Read an in depth comparison on Cisco vs. Microsoft for UC by ZK Research

Cisco TelePresence conferencing delivers exceptional face-to-face collaboration experiences through life-like video, audio, and content sharing.
Cisco WebEx Meeting Center provides easy-to-use, highly secure web conferencing for millions of users across platforms.
By bringing together these two powerful collaboration solutions, you can create an environment where people can easily work together, from anywhere, using a wide variety of endpoints and devices, including mobile.
Cisco TelePresence cloud services and solutions are built to deliver flexible deployment and service models with highly scalable conferencing, advanced media solutions for interoperability and the power to easily extend reach of video communities through secure intercompany and interprovider telepresence and options such as public telepresence suites.
Cisco Telepresence: At a Glance
Collaborate with Anyone, Anywhere, Anytime with Cisco WebEx

Easy to deploy and use, Cisco Unified Contact Center Express (Unified CCX) delivers a highly secure, available, virtual, and sophisticated customer interaction management solution for up to 400 agents. This integrated, comprehensive, contact center solution is intended for both formal and informal contact centers in midmarket, enterprise branch, and corporate departments. Unified CCX offers sophisticated call routing and comprehensive contact management capabilities. It includes an embedded reporting solution that offers a comprehensive view of contact center statistics at a glance.
Unified CCX provides customer segmentation with state-of-the-art, built-in, interactive voice response capability, and proactive customer service for a superior customer experience with integrated, outbound, call management capabilities. Multichannel capabilities include management of voice, email, web chat, and social media inquiries.
Three waves of customer care with Cisco Unified Contact Center Express
Data Center

Today, IT organizations assemble their data center environments from individual components. Their administrators spend significant amounts of time manually accomplishing basic integration tasks rather than focusing on more strategic, proactive initiatives. The industry is in a transition away from the rigid, inflexible platforms that result and moving toward more flexible, integrated, and virtualized environments.
The Cisco Unified Computing System™ is a next-generation data center platform that unites compute, network, storage access, and virtualization into a cohesive system designed to reduce total cost of ownership (TCO) and increase business agility. The system integrates a low-latency, lossless 10 Gigabit Ethernet unified network fabric with enterprise-class, x86-architecture servers. The system is an integrated, scalable, multichassis platform in which all resources participate in a unified management domain.
Delivering on Cisco’s Unified Computing Vision
Comparison of Blade Server Architecture: Cisco vs HP vs IBM
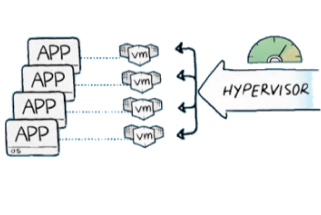
Virtualization is changing the face of data centers everywhere, bringing increased economy and agility to organizations of all sizes. As business organizations recognize the degree to which virtualization brings a competitive advantage, they are looking for the most advanced, effective, and efficient virtualization solutions that can further increase their competitive advantage.
Industry leaders Cisco and VMware combine the Cisco Unified Computing System™ with VMware vSphere software to bring outstanding support for virtual environments, enabling rapid application and infrastructure deployment with heightened security, availability, and performance. The reduced complexity of the Cisco Unified Computing System, coupled with extensive management integration with VMware vCenter, leads to increased business agility, greater return on investment (ROI), and lower total cost of ownership (TCO).
Why VMware?: A Comparative Analysis for New Virtualization Customers
VMware Horizon View: Your Cloud, Your Desktop Just Got Better
Cisco and VMware: Transforming the End User Desktop
Delivering on Cisco’s Unified Computing Vision
Comparison of Blade Server Architecture: Cisco vs HP vs IBM

Organizations of every type rely on the timely retrieval of information to facilitate transactions and decision making. While a typical organization is experiencing double-digit data growth, IT budgets, staffing, and traditional storage capabilities are not keeping pace. As a result, IT organizations are under constant pressure to employ more efficient storage strategies and increase the amount of data their staff can manage without additional headcount. Customers are looking to storage vendors for innovations to solve these challenges in the same way that server virtualization has enabled them to experience greater efficiency by pooling server resources and dynamically provisioning compute power according to business needs.
The EMC® VNX® family delivers industry-leading innovation and enterprise capabilities for file, block, and object storage in a scalable, easy-to-use solution. This next-generation storage platform combines powerful and flexible hardware with advanced efficiency, management, and protection software to meet the demanding needs of today’s enterprises. All of this is available in a choice of systems ranging from affordable entry-level solutions to high-performance, petabyte-capacity configurations servicing the most demanding application requirements. The VNX family includes the VNXe® series, purpose-built for the IT manager in smaller environments, and the VNX series, designed to meet the high-performance, high scalability requirements of midsize and large enterprises.
Introduction to the EMC VNX series
VMware vSAN – Radically Simple Hypervisor-Converged Storage
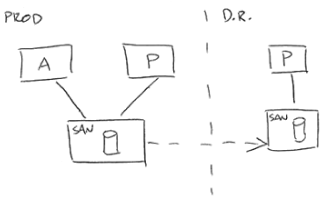
As a company, you want to make sure your data is safe and accessible, even in the worst of situations. However, the reality of it is much more complex.
Simply put, at Infranet we focus on three main questions:
• What are you doing today?
• How much downtime can you afford?
• What is your budget?
We look closely at what your business does and how backup plays a role in it. From here we can really gauge the importance of backup for your specific company. The next step is to learn our client’s recovery time objective (RTO) and recovery point objective (RPO). We see this time and again with customers who use solutions like tape. Sure, they backup a lot of info, then store it off site in a secure location. However when we speak to them about a Recovery Time Objective of under an hour suddenly they understand that this is nearly impossible.
The last step and many times the hardest part of the process is price. We must analyze in depth about how important it is from a business perspective. Downtime Calculators are used to help you understand what 8 hours of downtime looks like. A day of downtime. Even a week. These numbers get scary fast. For many customers they start to see how critical this is.
At Infranet we have a variety of solutions to address business continuity and backup needs, from file-level backup, complete server or workstation image backup, to full multiple data center mirroring (hot-site and cold-site).
With Infranet, worrying about recovering from a disaster is a thing of the past. Every engagement starts with a free consultation.
Infranet’s I-Care Cloud Solution provides a cloud based infrastructure to supplement or complement a client’s premise based solutions. Not everything may be a right fit for the cloud. This is where the expertise of a service provider that know the premise and the cloud equally well, and can position the right solution for your need. Just a few of the benefits of IaaS include:
- Scalability; resource is available as and when the client needs it and, therefore, there are no delays in expanding capacity or the wastage of unused capacity
- No investment in hardware; the underlying physical hardware that supports an IaaS service is set up and maintained by the cloud provider, saving the time and cost of doing so on the client side
- Utility style costing; the service can be accessed on demand and the client only pays for the resource that they actually use
- Location independence; the service can usually be accessed from any location as long as there is an internet connection and the security protocol of the cloud allows it
- Physical security of data center locations; services available through a public cloud, or private clouds hosted externally with the cloud provider, benefit from the physical security afforded to the servers which are hosted within a data center
- No single point of failure; if one server or network switch, for example, were to fail, the broader service would be unaffected due to the remaining multitude of hardware resources and redundancy configurations. For many services if one entire data center were to go offline, never mind one server, the IaaS service could still run successfully.
Microsoft 365 Business

Optimize Your IT with Infranet’s Tailored Microsoft 365 Services
Infranet proudly offers comprehensive Microsoft 365 (M365) services, uniquely tailored to meet the dynamic needs of small to medium-sized businesses. As a certified Microsoft partner, we don’t just implement M365, we revolutionize your operations, driving productivity, collaboration, and security to new heights.

Why Microsoft 365 is a Game-Changer
Imagine a workspace where collaboration happens effortlessly, security concerns are a thing of the past, and productivity is maximized. That’s what Microsoft 365 brings to your business.
With enhanced collaboration tools like Teams, SharePoint, and OneDrive, your team can work together in real-time from any location. This breaks down geographical barriers and fosters a cohesive work environment. Access to familiar applications such as Word, Excel, and PowerPoint, combined with advanced features, streamlines workflows and boosts efficiency.
When it comes to security, Microsoft 365 offers top-tier protection with advanced threat protection, data loss prevention, and multi-factor authentication. These features ensure your business data is safeguarded against cyber threats. Moreover, Microsoft 365’s scalability allows you to adjust services according to your business needs, ensuring cost efficiency by only paying for what you use.

Our Comprehensive Microsoft 365 Services
At Infranet, we believe in a holistic approach to M365 implementation, ensuring every step is tailored to your business needs.
We start with consultation and planning, conducting a thorough assessment of your current IT environment and business goals. This helps us develop a customized M365 strategy that aligns perfectly with your vision.
Our migration services ensure a seamless transition to M365 with minimal disruption to your daily operations. We handle the entire migration process with precision and care. Post-migration, we configure and integrate M365 to fit seamlessly into your existing processes and systems, maximizing efficiency.
We provide comprehensive training for your team, empowering them to make the most of M365’s features. Our ongoing support ensures continuous value from your investment. Additionally, we implement robust security measures and ensure your business stays compliant with industry regulations, protecting your data and maintaining your reputation.

Why Infranet is Your Ideal Partner
Choosing the right partner for your M365 implementation is crucial. Here’s why Infranet stands out.
With over two decades of experience, we bring a wealth of knowledge and skills to every project. Our team of certified professionals is dedicated to delivering successful M365 implementations. We understand the unique needs of businesses in North Carolina and Virginia. Our local presence means we provide personalized, on-the-ground support whenever you need it.
Your business goals are our priority. We work closely with you to ensure our solutions meet your specific needs, driving your business forward. Our portfolio is filled with successful M365 implementations for SMBs, showcasing our ability to deliver results and exceed expectations.
Ready to transform your business with Microsoft 365? Contact Infranet today to schedule a consultation and discover how our M365 services can help you achieve your business goals.
Security

Corporate networks are encountering the highest levels of change in history. No longer is work a place you go, but what you do; users are more mobile than ever before, requiring anywhere, anytime access to the enterprise and cloud-based resources. In response, the number and variety of mobile devices has surged, fueling the need to enable BYOD. In addition, unlike the monolithic software of the past, applications have evolved to be highly dynamic and multifaceted. Combined with the increasing velocity of internet-based threats, the trends of device proliferation, dynamic access use, and cloud have broken the legacy models of security.
A new approach is needed, one that unifies the network with security, ensures consistent protection across the enterprise, accelerates business innovation, and proactively protects you months before new threats impact the business. The Cisco ASA 5500-X Series Next-Generation Firewalls provide next-generation security capabilities at scale without requiring additional hardware modules. These appliances support services such as application visibility and control, web security essentials, intrusion prevention, remote access and cloud web security to provide an end-to-end, scalable security solution. Furthermore, integrating with Cisco ISE (Identity Services Engine) and Cisco AnyConnect Mobility solution, ASA 5500-X Series Next-Generation Firewalls provide a complete BYOD solution for high-end enterprises and small businesses alike
Cisco ASA Next Generation Firewalls At A Glance
Context Aware Security: Revolutionary Architecture, Evolutionary Deployment

The enterprise network today no longer sits within four secure walls. Employees today demand access to enterprise resources and their work via more mediums than ever before – by personal laptop from home networks, by tablets, and by smartphones. Mobility is a real game-changer, and enterprise networks need to grant access to this mobile workforce to keep workers productive. However, the shadow of security threats, data breaches, and the subsequent effects on the company still looms large.
Cisco Identity Services Engine (ISE) offers a centralized control point for comprehensive policy management and enforcement in a single RADIUS-based product from Cisco – the world leader in network security. It starts with rigorous identity enforcement that includes the industry first automatic device feed service to keep the profiling engine up-to-date with the latest smartphones, tablets, laptops, and even specialized network-enabled devices used in retail, healthcare, and manufacturing industries.
Cisco Identity Services Engine At A Glance
The Cisco BYOD Smart Solution

Regulatory compliance has become one of the strongest driving forces for implementing security. Depending on whom you ask, the passage of infosecurity laws and regulations can be viewed as one of the most important trends affecting information security or, conversely, the cause of the dangerous misperception that compliance equals security. This double-edged sword can wind up perpetuating unwarranted complacency. Although regulatory compliance certainly is a driver that must be taken into account in the implementation of your information security plan, it should be a result, not a goal.
Logs are immensely valuable for regulatory compliance. Many recent U.S. laws have clauses related to audit logging and the handling of those logs; just a few of the most important laws are the Health Insurance Portability and Accountability Act (HIPAA), the Gramm-Leach-Bliley Financial Services Modernization Act (GLBA), and the Sarbanes-Oxley Act (SOX). Centralized event logging across a variety of systems and applications, along with its analysis and reporting, all provide information to demonstrate the presence and effectiveness of the security controls implemented by organizations. These practices also help identify, reduce the impact of, and remedy a variety of security weaknesses and breaches in the organization. The importance of logs for regulatory compliance will only grow as other standards (such as PCI DSS, ISO2700x, ITIL, and COBIT) become the foundations of new regulations that are sure to emerge.

The Cisco® AnyConnect Secure Mobility solution is powered by the industry’s leading firewall: the Cisco ASA 5500 Series Adaptive Security Appliance. It offers a comprehensive suite of VPN access features along with powerful security features. It allows administrators to provision remote access through appropriate security policies for a variety of endpoints — from Mac or Windows environments to the latest iPad/iPhones and Android devices — using multiple access methods, such as the user acclaimed Cisco AnyConnect® Secure Mobility Client or the Cisco clientless portal for any web browser.
Cisco AnyConnect Secure Mobility Client: The industry’s leading client is a multi-faceted endpoint software product that not only provides VPN access through Secure Sockets Layer (SSL), including Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS) or IPsec Internet Key Exchange (IKEv2) protocols, but also offers enhanced security through various built-in modules, such as the Cisco Network Access Manager, the Cisco HostScan package, and Cisco AnyConnect Web Security module.
Secure Mobility: Collaborate from Anywhere on Any Allowed Device

Organizations everywhere struggle with the complexity of identifying and managing security risks within their environment. Infranet’s Vulnerability Management platform enables you to continuously scan your networks, endpoints, and cloud environments to quantify digital risks. Below is a summary of our capabilities:
External Vulnerability Assessment
Continuously scans internet-facing assets to understand your company’s digital footprint and quantify your business’s risk exposure
Quantify Your Cyber Risk Posture
A cloud-based dashboard provides visibility into continuous cyber risk assessment by incorporating all meaningful cyber risk indicators from your business. It identifies the highest-priority issues and alerts you to emerging risks before they escalate into real problems.
Internal Vulnerability Assessment
Continuously scans all of your internal IP-connected devices, while cataloging your core infrastructure, equipment/peripherals, workstations, Internet of things (IoT) devices, and personal (i.e., tablets) devices.
Host-Based Vulnerability Assessment
This capability extends visibility inside devices through continuous host-based monitoring to identify and categorize assets and reveal system misconfigurations, user behaviors, and vulnerabilities that put your organization at risk.
Consulting
Small Business